udp protocol id with tcp and udp port 1701 using VPN firewall
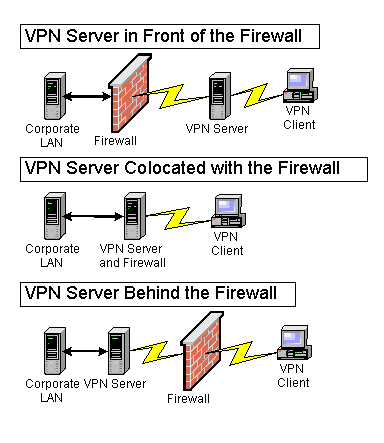
- A firewall is between the VPN server and the Internet.
- The VPN server is connected to the Internet and the firewall is between the VPN server and the intranet.
VPN server behind a firewall
A firewall is between the VPN Server and the internet for this configuration. In the intranet the VPN server is another resource connected to the perimeter network (screened subnet or DMZ-De Militarized Zone). The perimeter network is usually an IP network segment that connects to the Web servers and FTP servers. In addition to PPTP/L2TP/IPSec packet filters on the perimeter interface (described as VPN Server in front of Firewall) is needed. The filtration process is two fold
- Filters between the intranet computers and VPN server
- Filters between the internet and VPN server
Firewall filter configuration for Internet Interface
Firewall’s Internet Interface configuration giving the IP address and the port needed to be activated for traffic.
Inbound TrafficPPTPTo allow PPTP tunnel maintenance traffic from the PPTP client to the PPTP server.
To allow tunneled PPTP data from the PPTP client to the PPTP server.
Site to site VPN connection. VPN server acts as VPN client, Firewall filter is used in conjunction with PPTP filters that are configured on the server.
L2TP/IPsecTo allow IKE traffic to the VPN server.
To allow IPSec NAT-T traffic to the VPN server.
To allow IPSec ESP traffic to the VPN server.
|
Out Bound TrafficPPTPTo allow PPTP tunnel maintenance traffic from the PPTP server to the PPTP client.
To allow tunneled PPTP data from the PPTP server to the PPTP client.
Site to site VPN connection. VPN server acts as VPN client, Firewall filter is used in conjunction with PPTP filters that are configured on the server.
L2TP/IPsecTo allow IKE traffic from the VPN server.
To allow IPSec NAT-T traffic from the VPN server.
To allow IPSec ESP traffic from the VPN server.
|
Firewall Filter configuration for Perimeter Network Interface
Firewall Filter for Perimeter Network interface giving the IP addresses and ports for traffic
Inbound TrafficPPTPTo allow PPTP tunnel maintenance traffic from the VPN server to the VPN client.
To allow tunneled PPTP data from the VPN server to the VPN client.
Site to site VPN connection. VPN server acts as VPN client, Firewall filter is used in conjunction with PPTP filters that are configured on the server.
L2TP/IPSecTo allow IKE traffic from the VPN server.
To allow IPSec NAT-T traffic from the VPN server.
To allow IPSec ESP traffic from the VPN server.
|
Outbound TrafficPPTPTo allow PPTP tunnel maintenance traffic from the PPTP client to the PPTP server.
To allow tunneled PPTP data from the PPTP client to the PPTP server.
Site to site VPN connection. VPN server acts as VPN client, Firewall filter is used in conjunction with PPTP filters that are configured on the server.
L2TP/IPSecTo allow IKE traffic to the VPN server.
To allow IPSec NAT-T traffic to the VPN server.
To allow IPSec ESP traffic to the VPN server.
|
Note: No filters are required for L2TP traffic at UDP port 1701. All L2TP traffic at the firewall, including tunnel maintenance and tunneled data, is encrypted with IPSec ESP.
VPN Server in Front of a Firewall
The VPN server is connected directly to the internet. The firewall exists between the Intranet and the VPN server. Inbound traffic is decrypted and then forwarded to the firewall for filtering. Here firewall filtering is used to restrict VPN users from accessing specific intranet resources and non VPN users can be prevented from accessing these resources. The inbound and outbound packet filters need to be configured to allow only VPN traffic to and from the IP Address of the VPN server’s internet interface. You can also place an additional firewall between the VPN server and internet.
Firewall filter configuration for Internet Interface
Firewall’s Internet Interface configuration giving the IP address and the port needed to be activated for traffic.
Inbound TrafficPPTPTo allow PPTP tunnel maintenance to the VPN server.
To allow tunneled PPTP data to the VPN server.
Site to site VPN connection. The VPN server acts as client. TCP traffic is accepted after VPN server initiates connection.
L2TP/IPsecTo allow IKE traffic to the VPN server.
To allow L2TP traffic from the VPN client to the VPN server.
To allows IPSec NAT-T traffic from the VPN client to the VPN server.
|
Out boundPPTPTo allow PPTP tunnel maintenance traffic from the VPN server.
To allow tunneled PPTP data from the VPN server.
Site to site VPN connection. VPN server acts as VPN client. Send TCP traffic after VPN server initiates TCP connection.
L2TP/IPSecTo allow IKE traffic from the VPN server.
To allow L2TP traffic from the VPN server to the VPN client.
To allow IPSec NAT-T traffic from the VPN server to the VPN client
|
Firewall Products
Fire wall hardware of some suppliers are given below with the available port and data transfer rate
- Cisco- PIX Firewall 501 for PC’s (100 Mbps, 4 Ports, Cable Connectivity )
- Citrix- SonicWALL PRO 100 for PC’s (100 Mbps, 3 Ports, Cable Connectivity )
- WatchGuard Technologies- WatchGuard Firebox 700 for PC’s (100 Mbps, 3 Ports, Cable Connectivity)
- Network Associates – EPL-X250-NA-270I for UNIX based PC’s (100 Mbps, 2 Ports, Cable Connectivity)
- Symantec Norton – Firewall/VPN 100 for PC’s (100 Mbps, 4 Ports, Cable Connectivity )
- Lucent – VPN Firewall Brick 80 for PC’s,Mac OS amd UNIX (100 Mbps, 4 Ports, Cable Connectivity)
- Nokia – IP440 for PC’s (100 Mbps, 4 Ports, Cable Connectivity )
- Nortel – Alteon Switched Firewall 5105 for PC’s (4 Ports, Cable Connectivity )
Firewall VPN – Software suppliers and their products are given below. The choice of which depends on your system platform
- Symantec firewall VPN – Symantec Norton Personal Firewall 2003 – Full Version, PC Version, CD-ROM, For Win 2000 Pro / Win 98/ME / Win XP Pro.
- Network Associates – McAfee Firewall 4.0 – Full Version, PC version CD-ROM, For Win ME / Win 2000 Pro / Win 98 / Win XP Pro
- Check Point – FireWall-1 Next Generation Internet Gateway – Full Version, PC, Unix Version, License Qty: 25 nodes, CD-ROM, For Win 2000/NT 4.0 / Solaris / Win 98
- Lotus -IBM Firewall –License Only Version, PC, Unix Version, Volume License, License Qty: 1 gateway, For Win NT / AIX, Firewalls
- Computer Associates – ETrust Virus Defense Solution – PC, Unix Version, License Qty: 1 node, For Win 2000/NT 4.0 / Linux / NetWare / Win 98/ME, Firewalls, Antivirus
- Lucent -SecureConnect – Full Version, PC Version, License Qty: 1 router, CD-ROM, For Win 95/98 / Win NT 4.0 or later, Firewalls
Companies are subscribing to services that require internet access. To control risks and protect both individual computer and corporate networks firewalls as a part of internet security is necessary. These do not provide complete security but offer reasonable protection from unwanted intruders.

ExpressVPN Fast, anonymous browsing all over the world | ||
NordVPN Enjoy online privacy and security with a reliable VPN | ||
Cyber Ghost Browse anonymously with reliable security | ||
SurfShark Affordable and reliable VPN for secure browsing | ||
ZenMate Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |