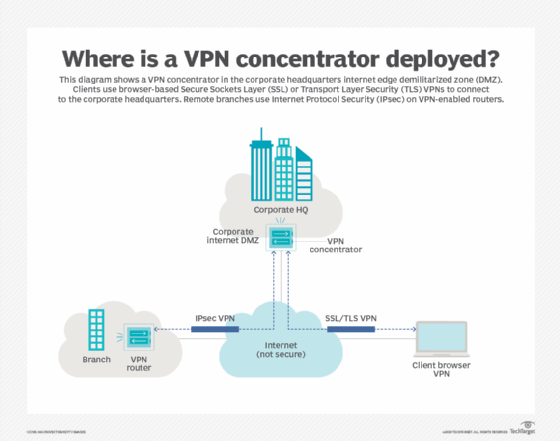
With more data breaches and cyber attacks occurring everyday, online security has never been more important. There’s also the threat of false public WiFi hotspots that harbor malicious software. VPN concentrators protect your online activities and sensitive data from hackers and other potential threats. The benefits of VPN concentrators are clear. Read on to learn more about this useful tool. Here are some of the benefits of VPN concentrators:
SSL encryption
A VPN concentrator creates a secure tunnel for receiving and transmitting data. The device also provides security for data exchange between systems within an organization and remote users. By using an SSL-encrypted tunnel, the device helps ensure data privacy. Additionally, the hardware components of a VPN concentrator are optimized to reduce the load on the CPU. A VPN concentrator can increase the overall efficiency of an organization’s network.
Choosing the right encryption protocol for a VPN concentrator can be an essential factor in securing data. For a small business, choosing the appropriate protocol for its needs is important. Similarly, companies looking for security should consider the security of data traffic. A VPN concentrator can provide different solutions depending on the requirements and budget of an organization. A strong encryption will protect servers from invasive attacks from the outside.
Dedicated hardware appliance
Dedicated hardware appliances for VPN concentrators require outstanding computational power to support multiple VPN connections. Dedicated hardware appliances are designed for large amounts of traffic and are generally optimized for encryption and decryption. They are also capable of supporting hundreds or even thousands of simultaneous VPN connections. Cisco sponsors a dynamic multipoint VPN (DMVPN) solution. A simple software-only VPN concentrator is also available. Dedicated hardware appliances have advantages over software-only options for several reasons.
Dedicated hardware appliances should support multiple protocols, such as OSPF. OSPF routes must be advertised and learned by all devices connected to the VPN concentrator. These devices advertise their routes to each other using a type 2 external route or LS Update message. The MX Security Appliance uses a number of types of outbound communication and may require a firewall configuration upstream to support these protocols. Dedicated hardware appliances should also be able to support multiple protocols.
Software-only solution
A VPN concentrator uses the IPsec or SSL encryption protocols to encrypt all data in transit. The SSL VPN protocol uses the TCP port 443 (secure socket layer) and IPsec uses TCP port 443. The TCP port is not used by most browsers, but port forwarding allows for customised configuration. The software allows for secure remote access to your network and servers. It also allows for SSL-128 or 256-bit encryption.
VPN concentrators are typically appliances with dedicated hardware for encryption. Cisco was among the first to create dynamic multipoint VPN. However, today, there are a number of software-only solutions on the market. If you’re on a budget, consider assembling your own VPN concentrator. OpenVPN is available as an open source project and pfSense has native Linux implementations. Other software-only concentrator solutions support DMVPN.
High-performance output
VPN concentrators are essential for organizations that require secure network communications. They offer high-performance output that can handle thousands of VPN tunnels at a time. They also offer expandability, enabling you to use as many as 10,000 VPNs for maximum efficiency. VPN concentrators redirect network traffic, and then reshape and encrypt it. These features make VPN concentrators ideal for organizations that have a high number of users.
VPN concentrators are especially important for companies that have multiple locations or travel salespeople. Many firewalls won’t let IPsec traffic, so they need a device that can handle the traffic. They also need to be able to coordinate with third parties, which can be difficult if all of the employees in a company use the same VPN. VPN concentrators ensure security and performance at a fraction of the cost of separate network connections.

ExpressVPN Fast, anonymous browsing all over the world | ||
NordVPN Enjoy online privacy and security with a reliable VPN | ||
Cyber Ghost Browse anonymously with reliable security | ||
SurfShark Affordable and reliable VPN for secure browsing | ||
ZenMate Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |