VPN requirements to setup a vpn software network tools.
- VPN Setup
- VPN Software Setup
- Requirements for VPN setup
- Configuration of VPN setup
Remote users have been able to connect servers using a variety of applications like outlook web access connection through the Exchange server. Wireless users connecting over the internet are more susceptible to security problems. VPN in a wireless environment provides the necessary security for wireless data transfer as the information sent is encrypted. VPN technologies have brought about a secure logical connection between two end points in a network. Setup for VPN may not require you to buy any extra hardware device or software. You may already have the technology that makes it possible to setup a VPN service. Sometimes you may just have to purchase a few accessories like VPN routers.
Hardware VPN vendors vouch that their products are safer and the software VPN vendors are not far behind. Whatever are the claims VPN is growing steadily and many attempts at increasing it security and performance is making it a lucrative solution to adapt. VPN solutions can either be hardware oriented or software oriented. The difference is very basic. It depends upon where the protocols are executed in the hardware device or on the computer system (where the operating system software of VPN client-server software is used). SSL VPN is a relative new clientless VPN technology that is come up as a challenge to IPSec VPN technology.
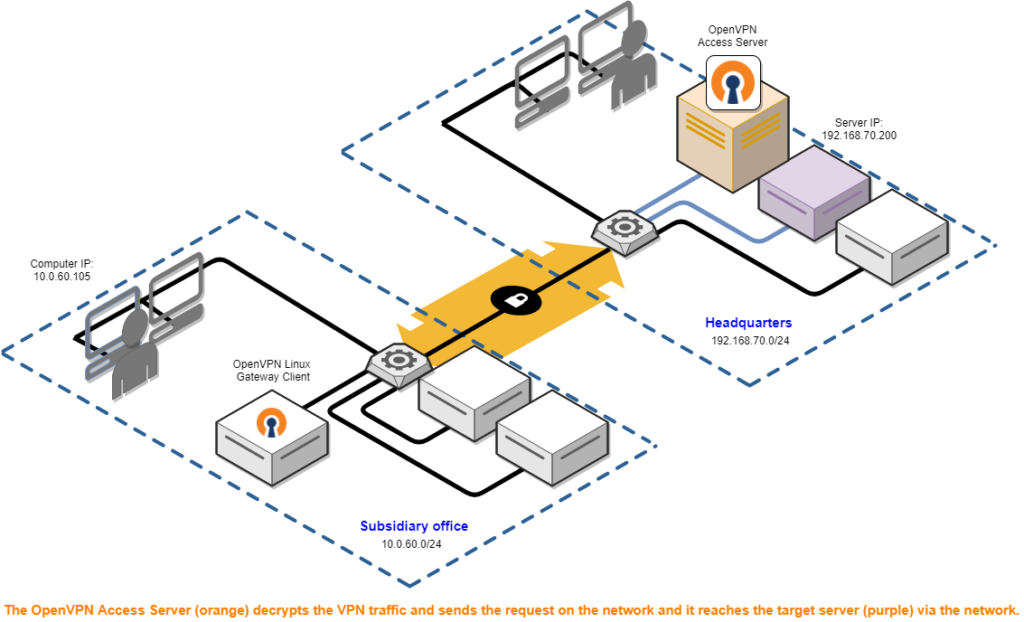
The thought behind VPN technology is very similar to QR codes. The goal of both services is to pass on a message which needs to be deciphered before returning the final information to the user. The process is different for the VPN and the QR code but the end result is the same.
VPN Software Setup
VPN setup depends upon a number of factors like what systems are involved in the end-to-end connection, servers or clients. Big corporations have a number of servers to improve on performance in various tasks that are carried out. Implementation of VPN for them will depend on the amount of work and the administrator’s solution offered to them. For client buy a software that the server is compatible with and setup VPN service. Some operating systems already give you the ability for VPN and all you need to know is how to setup VPN. Microsoft is a market leader and has monopoly over the market. It has incorporated VPN requirements into its operating systems or has provided service packs that could help you optimize your PC for VPN.
Requirements for VPN setup
In every setup you look at the requirements first and see whether it is possible to implement it with the available resources. If not ask yourself, what are the additional resources? For a windows based client-server system; the requirements would be a server (running server software, example Windows 2003) and a client (running client software, example Windows XP). For large corporations that have a secure network you would require additional servers.
- A server is required to supports the infrastructure of your network. It will act as a domain controller, DNS server, Certificate authority and DHCP-(Dynamic Host Configuration Protocol) server. Most networks already have this and the next step is setting up a certificate authority which is described in this article.
- A server that separately acts as your VPN server can prevent attacks or disruption of services within the network. It is best to place a firewall in front of the VPN server such that only VPN traffic is allowed into this server. The specific hardware that this server needs is two network interface cards; one to connect to the internet and the second to connect to the private corporate network.
- A server is needed to authenticate all the remote users attempting to access the private corporate network. RADIUS- Remote Authentication Dial In User Service is one mechanism, IAS-Internet Authentication Service is another mechanism that comes with the Server operating system. In other cases you could purchase additional software for authentication purpose. This is in case it does not come with the operating system you purchased. Authentication is done by VPN hardware products as well. These usually come bundled with software that does the work.
Continue to: Configuration of VPN components

ExpressVPN Fast, anonymous browsing all over the world | ||
NordVPN Enjoy online privacy and security with a reliable VPN | ||
Cyber Ghost Browse anonymously with reliable security | ||
SurfShark Affordable and reliable VPN for secure browsing | ||
ZenMate Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |