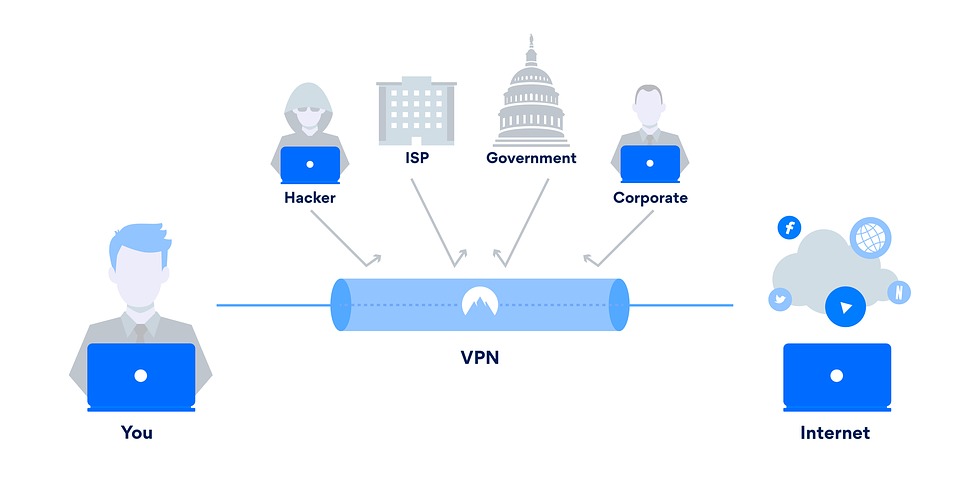
Different types of VPN encryption protocol connection and solutions
PPTP- Point-to-Point Tunneling Protocol
PPTP is one of VPN’s first protocols built on PPP to provide remote access for VPN solutions. PPTP encapsulates PPP packets using GRE-Generic routing Protocol. This had been modified to give PPTP the flexibility of handling protocols other than IP like IPX-Internet Packet Exchange, and NetBEUI- Network basic input/output system extended user interface. PPTP uses authentication mechanisms within PPP, i.e. PAP-Password Authentication Protocol. Various other authentication and security mechanism have been developed by Microsoft and is utilized in its Operating System software.
L2F- Layer Two Forwarding Protocol
This was designed to tunnel data from corporate sites to their respective users. A protocol primarily implemented in CISCO products, it differs from PPTP in a way that it does not depend on IP. This could work on alternate media like frame relays or ATM-Asynchronous transfer Mode. L2F accepts other authentication mechanisms and allows tunnels to support more than one connection. L2F uses PPP for authentication of remote user. The authentication is done twice, one at the ISP and the second at the gateway to the connecting LAN. It is also a Layer-2 protocol and handles IPX and NetBEUI as well.
L2TP – Layer Two Tunneling Protocol
The best features of PPTP and L2F were combined to form L2TP. It exists in the second layer (data link) of the OSI-Open Systems Interconnect model and so its name L2TP. Approved by IETF L2TP transport is defined for packet media, Frame relay, ATM and X.25 (Standard for packet switching networks defining layers 1, 2 and 3 of the OSI model). It has its own tunneling protocol and uses PPP’s PAP and other advanced mechanisms for authentication. Its encryption method is based on that of IPSec.
Internet Protocol Security (IPSec)
IPSec is a complete VPN protocol solution. Existing in the third layer of the OSI model it uses the IKE-Internet Key Exchange to exchange and manage cryptographic keys used in a data encryption session. IPSec uses a number of encryption technologies to provide confidentiality and data integrity. IPSec allows the sender to authenticate/encrypt or authenticate and encrypt each IP packet. For this it uses two modes either of which can be chosen dependent of situations of security and traffic.
- Transport mode for authentication and encryption of the transport segment of an IP packet
- Tunnel mode authenticates and encrypts the whole IP packet.
IPSec’s strong security measures are designed mainly for IP packets and cannot handle multi-protocol non-IP network environments like NetBEUI or IPX.
VPN is a virtual environment and its advantage is that it is not dependent entirely on physical setup for its organizational needs but on its logical setup. This is its boon and its bane as well.

ExpressVPN Fast, anonymous browsing all over the world | ||
NordVPN Enjoy online privacy and security with a reliable VPN | ||
Cyber Ghost Browse anonymously with reliable security | ||
SurfShark Affordable and reliable VPN for secure browsing | ||
ZenMate Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |