What is IPsec VPN? This virtual private network uses secure encryption and authentication of data packets. It is an open standard for creating encrypted communications between two computers on an Internet Protocol network. You can learn more about IPsec and how to use it in your virtual private network. Read on for more information about IPsec and how it works. To protect your privacy, you should always use a reputable VPN service. This is the safest way to access the Internet.

IPsec VPN is a type of virtual private network that allows you to securely access the internet from remote computers. This type of VPN does not require any end-user configuration and runs on the IP stack, so it can be used by virtually any application. It is designed to work on both Windows and Linux systems. To use IPsec, you should have a Cisco router. If your ISP doesn’t support it, you should be able to get a free trial from their website.
IPsec VPN uses encryption to transfer confidential data packets. Public keys are used to verify data packets. This prevents any tampering or forgery of the data. It can be used on both the network and the applications. IPsec VPN is ideal for business networking. It provides a secure connection to remote users. It’s not necessary to install software on the remote computer to access the corporate network.
IPsec encrypts data and encrypts the payload. This prevents forgery and other security risks. As long as the server implements a strong encryption, the connection between the two ends of the tunnel is completely secure. With this encryption, IPsec enables a secure communication between the two networks. The IPsec protocol provides protection for information. The security of this type of VPN is essential.
IPsec VPN is one of the safest methods to secure data transmissions. It uses encryption to ensure data security. By applying IPsec, a VPN can secure its connection without any modifications to the network. The protocol works at the network layer, so the IPsec protocol is transparent to applications. IPSec is the best option for secure data exchange. The disadvantages of IPSec are limited and it can cause inconvenient configurations.
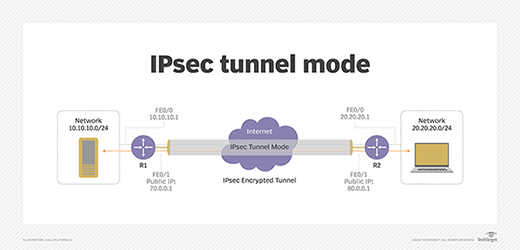
The IPsec protocol has two modes: Transport mode and Tunnel mode. Both of them encrypt the data that passes through the tunnel. The former secures data at the network layer, while the latter is asymmetric. With IPsec, the payload is encrypted and authenticated. Both IPsec modes are secure. The IPSec VPN protocol encrypts the payload. It is used to connect two different networks.
IPsec is transparent to applications. It is used for site-to-site and remote access VPNs. The difference between static and dynamic crypto maps is that the former is used for site-to-site IPsec-based VPNs. The latter is used for mobile data and remote access. The static crypto maps are used for site-to-site IPsec networks. The dynamic ones are used for remote access VPNs.
The IPsec protocol was originally designed to allow remote users to connect to a network via the Internet without the need for a dedicated line. This method is known as tunneling. In IPsec, two-way encryption is used to prevent data from being intercepted by a third party. During the first phase, the encryption of data is done using public keys. For the second phase, the IPsec protocols use protocol 50.
IPSec VPN is a secure VPN that protects IP traffic. The protocol encrypts data and also includes a security certificate. IPSec is used to secure the general IP traffic between two computers. Its use is popular for remote IT support, where employees work from home. The VPN requires a special application to be installed on the server. This application will authenticate remote users and ensure their security.
IPsec VPNs have two main modes, called tunnel mode and transport mode. In the first, the IPsec tunnel is secured by an IPsec certificate. This is a secure VPN with a high MSS, which means that it’s more secure than its counterparts. It is also flexible and can work with legacy systems. Besides, it can allow remote workers to connect to a network that’s not connected to their company’s internal network.

ExpressVPN Fast, anonymous browsing all over the world | ||
NordVPN Enjoy online privacy and security with a reliable VPN | ||
Cyber Ghost Browse anonymously with reliable security | ||
SurfShark Affordable and reliable VPN for secure browsing | ||
ZenMate Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |