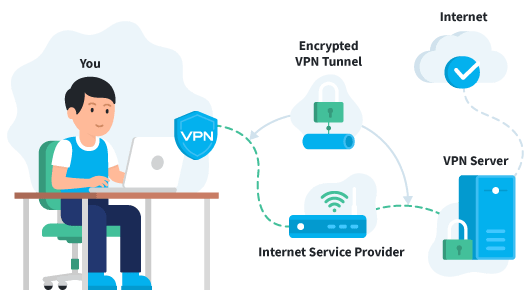
VPN setup procedures for various types of VPN and working
Secure access and privacy is provided by the various security procedures like encryption, authentication procedures, Firewalls and other protocols.
Purposes that protocols involve:
- Data encryption at the sending end
- Creation of a tunnel where data in the form of packets is encapsulated in the existing TCP/IP. Packets that that is not encrypted cannot pass through
- Decryption of data after reception at the receiving end
- Additional level of security involving not only passwords but also the senders and receivers network addresses.
Setup VPN
The types of VPN determines it setup. VPN can be a client initiated ‘remote access VPN’ or ‘site to site’ based VPN that is either intranet or extranet. You may want to know how to install VPN? There are a variety of methods depending on the hardware, software and protocols adopted. There are no standards in the industry and therefore for any setup you would need to find out if the hardware and software of the senders and receivers are compatible to set up a VPN. Most of the users that have trouble are the clients on a remote access VPN.
Setup of a remote access VPN
A remote access VPN client consists of a software client installed on the remote computer and a router.
- The VPN router comes with software. All you need to do is install the given software and follow the procedure. You need to have a VPN account with the ISP provider. You also need to know your IP address as well as that of the other computer with which you want secure communication. A word of caution with regard to this approach is that the sender may have to use the same software/hardware you are using.
- Many operating systems have incorporated VPN client software. A wizard will guide you through the various steps in some operating systems. You need to have a little knowledge of protocols (PPTP, L2F, IPSec etc.) and port addresses as these determine your type of connection and level of security.
- At the server side the VPN server configuration depends on whether you want to have a separate server or use the same server that you use for other tasks in the organization. In case you use the same server you may not get a good throughput even though you have a broadband connection since the server is loaded. A server setup is a more professional task but isn’t difficult if you have proper knowledge of processes.
Setup of Site to Site VPN
Since a site to site connection is between two servers in an intranet or an extranet all you need to do is configure the answering and calling routers.
- Configure VPN on the Answering Router
- Configure the Demand-dial Interface on the Answering Router
- Configure VPN on the Calling Router
- Configure the Demand-dial Interface on the Calling Router
- Create a Network Rule Defining the Route Relationship between the servers
- Create Access Rules allowing Traffic between servers
- Test and Confirm the Remote Access Policy Configuration on the Answering and Calling Routers
Encryption and Protocols are a technical subjects and choice of these is related to costs and security. Whatever you choose remember that security is a daily issue and you need to constantly monitor it.

ExpressVPN Fast, anonymous browsing all over the world | ||
NordVPN Enjoy online privacy and security with a reliable VPN | ||
Cyber Ghost Browse anonymously with reliable security | ||
SurfShark Affordable and reliable VPN for secure browsing | ||
ZenMate Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |