VPN Security protocols with overview on network security
- Is VPN a secured network?
- Incidents that undermine security
- Networking security Overview
- Overview of VPN
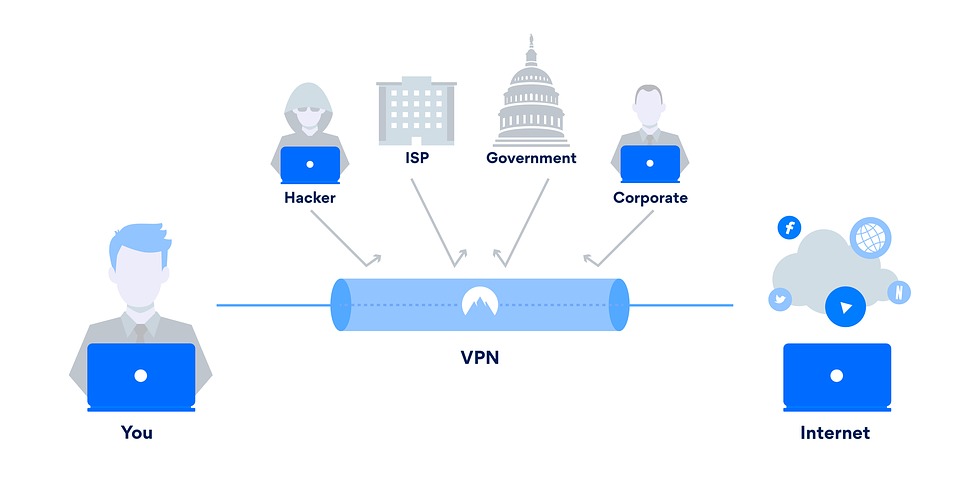
Network Security, VPN or not, is a major concern. Security in a VPN is pre-eminent to its usage as an alternative to WAN. Organizations think VPN is a secure network. Contrary to this belief you find many reports or alerts on the internet that discloses loop holes in a VPN. VPN is really a tunnel of information and protects information between your application and the server. Complete end-to-end security is not a guarantee. System patches, Antivirus software’s with firewalls, additional encryption of data between user application and server application and vigilance on the part of the administrator is needed. For any computer user there are innumerous attacks on his system. These may be a probe or a scan. Possibilities are account compromise or root compromise when having multiple users or a server user accounts. It can also be packet sniffing, denial of service, exploitation of trust (phishing), malicious code, and Internet infrastructure attacks.
- A probe is an attempt to discover information about the system. It usually is followed by a more serious security event.
- A scan is automated done by some software tools. Scans result in changing the configuration of the systems. Once this is done a more specific attack can be made as the machine is open to intruders.
- An account compromise is the unauthorized use of a user account. It can result in data theft/loss. The account privileges determine the level of damage. A system level privilege can cause more damage. In UNIX systems a root compromise is when the intruder gets unlimited access to the system.
- Packet sniffer’s are programs the captures information from packets as they travel on the net. Depending on the information gained they can gain access to your system and cause damage.
- You are using a service on a network. If your service is important then a denial of service is to stop you from using your service by disruption in physical connections, Manipulation of data in transit, or flooding the network so that the service you use becomes limited.
- In a large network the many individual systems have to run common commands. These systems therefore check a set of files with the other systems that are permitted to use those commands. Attackers use this loop hole and forge identities to appear as a system that can be trusted thus gaining unauthorized access.
- Malicious code is a program that has undesirable results. These are viruses, Trojan horses and worms. These can lead to data loss, denial of service and other types of security incidents
- Attacks on key systems that support the internet and its working hinder operation of the internet.
Networking security Overview
The potential problems that can lead to a security problem in case of a client server setup of an organizations is
- The Users System
The users system should have a virus protection and its operating system should have all the updates and patches. Also necessary is the applications security and their respective patches. (MS-outlook has been vulnerable before). Another major factor is the amount of time a given system is actively connected to a network. (Cable modems or Ethernet connections have been more vulnerable to port scanner intruders where as dial-up users are less prone to virus infections or file access related risks) - The Intermediate Network
The ISP has to route data from a site or IP address to you and vice versa in case of a two way communication. Your information can be intercepted and decrypted information read by a DNS-(Domain Name System) Server if your packet is routed through their system - The Destination Network
The network that you are communicating with may not be secure. If this happens, you cannot be assured of security to your system and privacy of your data. - The Server
Server operating system and applications are constantly under threats of new viruses, intrusions, and worms. Administrators are always checking for security risks due to compromised usernames and passwords.
- Fiber-optic fast connection
- Speed of up to 40Mbps
- Upload speeds up to 5Mbps
- 99.9% network reliability
Continue to: Overview of VPN Security

ExpressVPN Fast, anonymous browsing all over the world | ||
NordVPN Enjoy online privacy and security with a reliable VPN | ||
Cyber Ghost Browse anonymously with reliable security | ||
SurfShark Affordable and reliable VPN for secure browsing | ||
ZenMate Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |