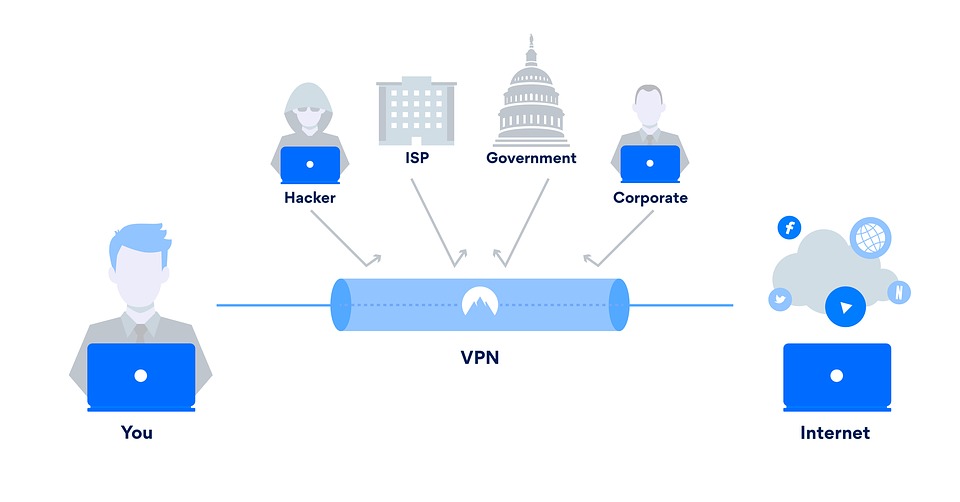
VPN security information and a general overview
The intermediate Network
Vpn security is most beneficial in this segment. All communications VPN client to VPN server is encrypted and encapsulated and the intermediate machines that route the packets only can read the source and destination IP addresses.
The Destination Network
Encrypted Data that reaches the server is decrypted and sent to the required destination within the network. The protection of data by the VPN connection ends here and any further protection of the data is the responsibility of the server and the LAN security systems.
The Server
The end point-to-end point of communication is not a completely secure
if at the destination end the application does not receive the decrypted data. This happens when the VPN server is not the same machine as the application server and then data has to be sent to the application through the LAN which may not be secure. VPN split tunnel security becomes important if the server handles both intranet and internet traffic.
Setting up a Secure VPN
Security at the endpoints is necessary and cannot be ignored. Antivirus software’s with Firewall and other intrusion detection systems are necessary. VPN’s security deals mainly in the transit of information from one end point to the other. In this scenario the major technique that ensures safety is the VPN encryption technology and the VPN protocols that are used. A new technology that is gaining popularity is SSL VPN, which is an altogether a different type of VPN. It cannot be compared with other IP VPN protocols.
Encryption
Encryption of data and secure authentication is a way of providing security. Kerberos, S/Key and DESlogin are some methods used in authentication. In encryption The various methods used are
- RSA- (Ron Shamir Adleman), which is a popular method in public key encryption and digital signatures.
- DES- (Data Encryption standard) is an official standard and forms the basis for ATM’s-(Automatic Teller Machines) PIN authentication.
- Blowfish is a symmetric block cipher and is gaining popularity as a strong encryption algorithm.
- IDEA-(International Data Encryption Algorithm) is being implemented in hardware chipsets making the algorithm even faster than the others.
- SEAL- (Software-optimized Encryption Algorithm) is a Stream-Cipher (encryption is in continuous streams rather than blocks of data) and so is faster.
- RC4 is useful when a new key is chosen for each message
VPN Protocols
VPN creates a secure “ tunnel ” through the public network and protocols establish this tunnel. Security could depend on a number of factors like Client-server systems, Level of security, performance issues and network resources accessed.
PPTP
- PPTP uses the same types of authentication as PPP (PAP, SPAP, CHAP, MS-CHAP, EAP).
- PPTP establishes the tunnel but does not provide encryption. It is used in conjunction with the Microsoft Point-to-Point Encryption (MPPE) protocol to create a secure VPN.
- PPTP client are available for Linux, Macintosh OS 9.x
- Firewall appliance and other enterprise level software including ISA Server, Cisco PIX, SonicWall and some models of WatchGuard support PPTP
L2TP
- Authentication is the same as in PPP. It provides an extra level of security by providing computer authentication also and can be used on non-IP networks such as ATM, frame relay and X.25.
- L2TP requires the use of digital certificates. It uses IPSec’s ESP-(Encapsulating Security Payload) protocol to provide encryption
- The L2TP client is built into Windows 2000, XP and 2003. Service packs give you the availability of client software for other operating systems.
- Firewall products and enterprise level software like ISA Server, CheckPoint, Cisco PIX, and WatchGuard support L2TP.
IPSec
- Authentication involves IKE-(Internet Key Exchange) protocol with either digital certificates or with a preshared key.
- IPSec protocol is more famously known for encryption in conjunction with the L2TP tunneling protocol.
- IPSec support is included in Windows 2000/XP/2003 operating systems. Cisco, CheckPoint and other Gateway vendors provide provide client software for IPSec-based VPNs.
- VPN appliances that implement IPSec include Cisco’s VPN Concentrators, CISCO PIX firewalls, NetScreen, SonicWall, and WatchGuard appliances. Enterprise level software firewalls like ISA Server, CheckPoint and Symantec Enterprise Firewall also support IPSec VPNs.
Virtual private networking is often the best and the most cost effective way to provide remote access to your company network. Know the protocols and their implementation to make a decision. This affects both performance and security.

ExpressVPN Fast, anonymous browsing all over the world | ||
NordVPN Enjoy online privacy and security with a reliable VPN | ||
Cyber Ghost Browse anonymously with reliable security | ||
SurfShark Affordable and reliable VPN for secure browsing | ||
ZenMate Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |