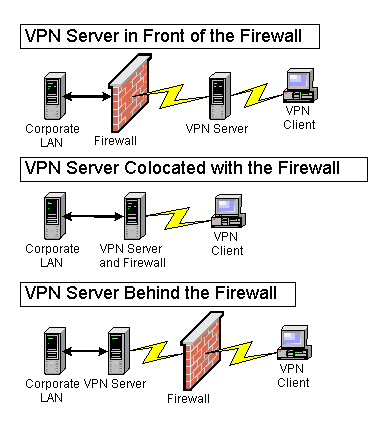
VPN firewall setup techniques and protection provided
Firewall is security schemes on the computer preventing unauthorized access from a network to any application or service on the computer. Network firewall allows and blocks traffic into and out of a computer or the network. This monitoring can be done by software on the same machine or in the router or in case of large networks on a stand alone machine. More complicated systems could be a number of routers or a number of systems that block unwanted access to a private network.
What does a firewall protect?
Hackers have used ingenuity to abuse unprotected computers. Firewalls block out these unscrupulous elements from achieving their ends. These elements try many methods and security is designed to prevent these methods. The many methods that firewall stops them are:
- Remote Login is where a person is able to connect to your computer and control it in some way. The control may be accessing files on your computer or even running programs on your computer.
- Application Backdoor is using a feature of remote access granted by some application programs. (This is because some programs allow some level of control or it is some bug or hidden access that you are unaware of).
- SMTP session hijacking is one of the methods used by spammers. They redirect junk e-mail through the SMTP server of an unsuspecting host (gaining unauthorized access to a list of email addresses). This makes it difficult to find the actual sender of the spam.
- Operating systems sometimes provide insufficient security controls or have bugs that experienced hackers use; to gain remote access to a computer or network.
- Denial of Service is an attempt to slow the web server down and eventually make it crash. The hacker achieves this by sending the server a request to connect to it. The server responds with an acknowledgement and starts to establish the connection by creating a session. The session requires connecting to the computer system that made the request but the system that made the request is not found by the session. This is because the path the information takes is redirected to a different router using ICMP-(Internet Control Message Protocol). The hacker inundates the server with these unanswerable session requests causing it to slow down and eventually crash causing a denial of service to the many legitimate users who are attempting to connect to the web server.
- E-mail bombs are more personal than denial of service. Hundreds or thousands of the same mail is sent to you so that your inbox cannot accept any more messages. Thus preventing others from sending you mail.
- Macros are simple procedures that are run within an application program. The script of the procedure is called a macro. Hackers write scripts in an application program to destroy data or prevent the application from working properly.
- Computer Viruses are the most well known threat to computers. They are of different types from harmless messages to very harmful programs that copies it self onto computers and spreads to other computers. These can even erase all your data.
- Spam is electronic equivalent of junk mail. These often contain links to websites. Sometimes if you click on these mails you may accept a cookie that provides a backdoor entry to your computer.
- Source Routing is done by a router arbitrarily specifying the route a packet takes over a network. Private networks look at the source IP address of the source before it routes the packet to the desired destination within the network. Hackers use this IP Address to make information appear as though it has come from a trusted source.
Firewall Techniques
There are several techniques used in firewalls. Mostly they are used in combination for effective security.
- Packet Filtering is accomplished by a software routine which discards packets that are not from trusted sources. This is done by analyzing incoming data packets based on one or more criteria such as address, range of addresses and type (e-mail, file transfer, etc.). Most packet filters are software’s in routers (screening routers) that allow the internet connection to a private network.
- Proxy is a break in the connection between the sender and the receiver by a computer or a router. It functions as an intermediary between a client and a server preventing invasion of the private network. Proxies are mostly used in conjunction with NAT-Network Address Translation. HTTP proxy is used for web proxy and FTP proxy is used for File transfers. These are known as application level proxies or application level gateways. A circuit-level proxy or generic proxy supports multiple applications. ‘SOCKS’ is a generic based proxy server.
- Network Address Translation allows only one IP address to be shown to the outside world. Implemented in a router, firewall or PC it connects private addresses of a machine to one or more public addresses on the internet. Reverse connections are made for packets that come from the internet to private machines. Public IP addresses are conserved as well as private IP addresses remain a secret thus preventing some of the first level attacks that can occur on the net.
- Stateful Inspection is a firewall technology that ensures that the inbound packets are the result of an outbound request. This way it blocks attackers from sending harmful or not requested packets to a network.
Continue to: Firewall setup for VPN

ExpressVPN Fast, anonymous browsing all over the world | ||
NordVPN Enjoy online privacy and security with a reliable VPN | ||
Cyber Ghost Browse anonymously with reliable security | ||
SurfShark Affordable and reliable VPN for secure browsing | ||
ZenMate Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |