Understanding VPN technology along with port and tunnel.
- The technology to ensure security on the internet
- Tunnel
- Different Protocols of VPN
VPN technology uses internet as its backbone for communication. The internet was designed to provide communication even if a part of the network was damaged or destroyed. This was possible due to routers that would direct traffic on alternative routes when the direct route was not available. The earliest users were scientists and librarians. No home or office computers used the internet. Today almost everyone uses the net and with the increase in the users many nefarious characters started hacking and creating viruses.
Present concerns of security and performance were not there when the internet started. The TCP/IP and the internet were not designed for this and are still evolving to issues of security and performance. VPN technology is now serving as a reliable substitute to dedicated leased lines or WAN. Standards for network security on IP networks are now evolving to create virtual private networks. Yet for all these processes are not deployed to a great extent.
The technology to ensure security on the internet has to address concerns like
- Authentication: Data originating from the source that it claims.
- Access Control: Permitting authorized user’s access while restricting unauthorized users access to the network or its facilities.
- Privacy: Preventing anyone copying, viewing or tampering with data that is not theirs thus providing the needed confidentiality as well as data integrity.
Private Networks that are not VPN based, use leased lines. These connections were for communication of information related only to a given corporate. WAN was widespread even if it were a branch office or few users outside the centralized network. With globalization, enterprises are expanding beyond vistas ever imagined. The traditional Private networks are unable to cope with the growth. Public Networks are rising to the challenge with password based systems and challenge response systems such as CHAP- Challenge Handshake Authentication Protocol, RADIUS – Remote Authentication Dial-In User Service, hardware tokens and digital certificates. These systems are used to authenticate users on a VPN and provide access control to network resources. Privacy of data is achieved through the various encryption algorithms like RSA, DES/3DES, BLOWFISH, IDEA, SEAL, and RC4.
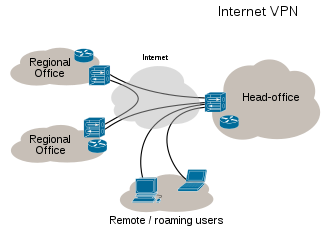
VPN Tunnel
Private leased line networks had hard-wired dedicated connections from single corporate customers. Extending the idea of dedicated connection to the internet, a number of protocols have sprung up. These create tunnels, allowing users to encapsulate their data in IP packets, which hide routing and switching information from both the sender and receiver. Snooping is thus prevented using encryption.
Any communication involves two end points and usually in VPN technology it is between ‘Client-to-LAN’ and ‘LAN-to-LAN’. In a ‘client-to-LAN’ case the client has a special client VPN software that they run to communicate with the gateway, protecting the receivers LAN. In case of ‘LAN-to-LAN’ connections security gateways at each end point is the interface between the tunnel and the LAN. A security gateway is either a VPN router or a firewall.
WAN hardware equipment consists of modem banks and multiple frame relay circuits which can use any transport medium for transmission of data. There is a reduction of equipment needed for a VPN when compared to a WAN. VPN hardware and software setup and maintenance cost is also reduced and many companies now outsource VPN to service providers.
Continue to: Different Protocols of VPN

 | ExpressVPN Fast, anonymous browsing all over the world | |
NordVPN Enjoy online privacy and security with a reliable VPN | ||
 | Cyber Ghost Browse anonymously with reliable security | |
SurfShark Affordable and reliable VPN for secure browsing | ||
Private VPN Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |