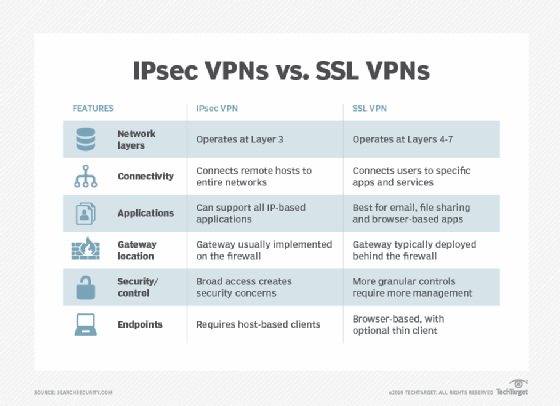
Complete information on IPSEC Vs SSL VPN, pros and cons
- Application layer proxies are truly clientless and operate with all operating systems and browsers. It protects internal data from direct exposure to the Internet since the application (SSL VPN appliance) terminates and translates all the application level protocols before it reaches the network. Authentication and policy is done before allowing connections to application servers, this boost security. This supports e-mail and web based traffic and is the simplest form of SSL VPN ‘s. To provide additional functionality other applications need to be web enabled.
- Protocol redirectors are not truly clientless but are more flexible than application level proxy. A mini client is downloaded from the gateway and works by redirecting traffic. If an application that is not web enabled makes a connection then the connection is captured and encapsulated in a SSL tunnel. From the SSL gateway it is then proxied to the destination. The advantage of this approach is that it works on TCP and UDP protocols. It also supports dynamic port allocation. In this a VPN port number is dynamically allocated. A disadvantage is the inability of the client software being installed on the client machine in an internet caf é because of administrator privileges preventing the user installing software’s on the system.
- The Remote control enhances terminal services of Windows or Citrix Metaframe by adding SSL VPN functionality and Web Browser based support. Addition of an application to the remote control desktop gives the application SSL VPN functionality. This has limitations because application residing on the desktop cannot be used directly. The advantages being ability of read and update a document centrally without downloading it. Low speed connections or poor quality of connection is not a problem as work is restarted without any loss.
SSL works at the Layer 4 and an SSL connection is established with a handshake between client and server.
- A connection is made and the server is authenticated to the client, verifying that a server’s certificate and public ID are valid and have been issued by a trusted certificate authority.
- The client and server negotiate. They select algorithms for encryption that both the server and client support.
- The client may then be authenticated to the server,
- An authenticated and encrypted SSL connection can be established.
Different access privileges can be given to different users providing detailed access control. Since SSL is pre installed in every major web browser it does not require additional software. SSL VPN can be extended to any location and can utilize TCP/UDP transport systems. SSL VPN can provide access from corporate managed devices and can traverse NAT devices and proxy based firewalls. Split tunneling (the ability simultaneous access to Internet and internal corporate resources) is controlled with SSL VPN s. Most SSL VPN ‘s are appliances that can handle large number of concurrent users. It can be used over a mobile network of GSM with GPRS or EDGE and suffer from lesser packet fragmentation. It has a better compression mechanism.
Advantages of SSL VPN
- Cost saving is of prime importance because most web browsers already have SSL functionality and are freely available. SSL VPN clients are priced lesser compared to that of IPSec VPN.
- Any machine can use SSL VPN for a secure access. VPN client platforms are available for most operating systems(Linux, Windows 2000/XP, Apple Mac, Palm OS, Symbian pocket PC)
- Client mobility is possible as the client can connect from any machine (laptop, corporate desk top and Internet cafe) across dial up, DSL, GPRS and leased lines. SSL VPN is not bound by the client IP. It is also mobile and not fixed as in the case of IPSec.
- Network Address Translation and NAT traversal mechanism created problems in IPSec. These do not exist with SSL VPN ‘s.
- SSL based VPN’s often communicate on the port used for Secure HTTP. This port is, one of the few ports on which outbound access is normally allowed in a corporate network.Usual security infrastructure with firewall rules prevents outbound traffic on other ports. These ports have to be disabled manually during the setup of a remote access server for IPSec.
- Once a SSL VPN session is terminated all the contents of downloaded files as securely deleted. This avoids attachments and other corporate data being left on an un-trusted machine at the time of ‘log off’.
- Application level filters of SSL especially when application level proxy is used can block worms and viruses at the gateway.
Disadvantages of SSL VPN
- If the client platform security is compromised then security based problems can arise. This is more prominent when an internet caf é is used for SSL VPN . Scrutiny of the client is a necessity in such circumstance and many vendors of SSL VPN have developed mechanism to boost the trust associated with an un-trusted client connection.
- Active-X and Java applets which are methods used to enable SSL VPN are the same methods used by malicious hackers. In such an environment client integrity scanning becomes important. An applet is therefore downloaded on the client that looks for good and bad files and for any spying or listening done on the ports. This process is not foolproof and limits the types of clients that can be connected.
- With enterprise based VPN solution a strong authentication is needed but with SSL VPN when ever the user logs off the system their credentials are wiped off from the system.
- SSL VPN is relatively simple and if any user’s logon credentials are compromised then a remote hacker can abuse the SSL VPN system. The related problem is that no activity alert is on the server. If this was there then monitoring of persons logging in and their activity is monitored. If suspect action is viewed the connection can be terminated.
- The major block to deployment of SSL VPN’s is application support. Vendors add additional support through the use of protocol redirectors. This requires some ‘user knowledge’.
- All sessions from an SSL VPN are proxied from a single address and so all client sessions originate from this single IP. For an SSL VPN the network administrator cannot allocate privileges using source IP addressing. This reduces the ability to filter and control traffic based on IP source.
The factors that need to be looked at before making a choice between the two are
- What are the security risks involved?
- Is there scalability and flexibility?
- What are the protocols that I need?
SSL VPN s has significant advantages over the IPSec alternatives; yet a knowledgeable approach of your requirements is needed.

 | ExpressVPN Fast, anonymous browsing all over the world | |
NordVPN Enjoy online privacy and security with a reliable VPN | ||
 | Cyber Ghost Browse anonymously with reliable security | |
SurfShark Affordable and reliable VPN for secure browsing | ||
Private VPN Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |