Comparisons of IPSEC Vs SSL and their performance
- The layers of IP
- IPSec VPN
- Advantages of IPSec VPN
- Disadvantages of IPSec VPN
- All you need to know of SSL
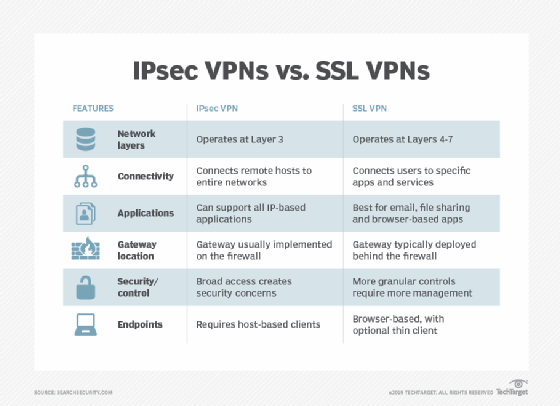
Internet Protocol security is evolving and a discussion of IPSec or SSL should be relative to the version of IP. IPv4 did not offer many secure features to IPSec VPN software when compared to IPv6. Internet protocol operates on the TCP/IP model which can be compared to the OSI model of 7 layers. A major difference it that of the transport layer of TCP/IP, which does not always guaranteed reliable delivery of packets when compared to that of OSI. The layers of IP are
5. Application: authentication, compression, and end user services
4. Transport: handles the flow of data between systems and provides access to the network for applications via the BSD socket library
3. Network: packet routing
2. Link: Kernel OS/device driver interface to the network interface on the computer.
1. Physical Layer (cables and connectors)
All about IPSec VPN
IPSec protocol provides authentication, verification and encryption between the VPN IPSec server and the VPN IPSec client at the IP networking layer. IPSec was developed by the internet engineering task force for security at packet level so as to transmit data over public insecure networks. IPsec VPN provides data authentication, integrity and confidentially with AH- authentication header, ESP-Encapsulation security payload and IKE-internet key exchange. IPSec VPN tunnel protects packets from being tampered or retransmitted along the Ipsec VPN route. This is done through the concept of security association (SA is a logical connection between two devices transferring data). Key management protocols are not a part of IPSec. The services that IPSec is designed to provide at the Network layer is Access control, Connectionless integrity, Origin authentication, Replay protection, and Privacy/confidentiality. The quality of these services depends upon the ‘Security administrator’. Several different security technologies to implement confidentiality, integrity, and authenticity are combined into IPSec.
- Public key cryptography to guarantee the identity of the two parties and avoid intermediate attacks
- Encryption algorithms, such as DES,3DES for encrypting the data
- Packet authentication is provided by HMAC a Keyed hash algorithms in conjunction with traditional hash algorithms such as MD5 or SHA.
- Digital certificates signed by a certificate authority to act as digital ID cards.
IPSec provides different types of protection and operates in different modes(transport mode and tunnel mode). In the transport mode of IPSec operation, authentication is direct between a client and a server workstation. This process is secure if the server/workstation shares a ‘protected secret key’ authentication process. When AH is used in transport mode the whole packet is authenticated, but confidentiality is not provided. In tunnel mode, authentication is done via the corporate firewall. Based on the method used AH or ESP the whole packet is either authenticated, encrypted or both.
Advantages of IPSec VPN
- Universally applicable as it can protect a mixture of applications protocols running over a complex combination of media. . It can provide security and communicate with different types of networks from around the world.
- Scalable as IPSec can be applied in networks of all sizes.
- Its security is in the Network Layer. IPSec’s goal is to develop something with the OS at Layer3 which means no changes are required to applications to provide security for diverse range of protocols. Also it is not affected by lower level data carrying protocols and higher level applications.
- IPSec is not limited to specific applications but is application independent. Whatever be the application the data will traverse the network, routed by IP making it IPSec compatible.
Disadvantages of IPSec VPN
- Encryption of small packets generates a large overhead. This diminishes network performance.
- IPSec is complex. It has a great many features and options. Choosing and setting an option is a bit difficult. Complexity also increases the probability of weakness or loop holes being discovered.
- Firewalls are preconfigured rules and IPSec encrypts these rules in the packet which defeats the purpose of a firewall. A solution for this could be firewall along with an IPSec gateway.
- The security of IPSec is easily affected by weakness or vulnerability’s in the specific methods for key exchange, in hashing or encryption algorithms. The DES encryption algorithm is now susceptible to brute-force attacks using readily available software and hardware. Brute force attacks are methods to decrypt data by simply trying every possible key value.
- An IPSec gateway system needs to be secure if this is compromised then No system can be trusted if the underlying machine has been subverted.
- IPSec can’t provide the same end-end security as it is not working between users or applications but between machines.
IPSec must be combined with security measures like well configured firewalls, intrusion detection systems, and many others. The future demands scalability and flexibility. Compatibility with NAT from this protocol is an issue. Its weakness lies in using other encryption methods. Inbuilt intrusion detection and prevention should be made possible.
Continue to: All you need to know of SSL VPN

ExpressVPN Fast, anonymous browsing all over the world | ||
NordVPN Enjoy online privacy and security with a reliable VPN | ||
Cyber Ghost Browse anonymously with reliable security | ||
SurfShark Affordable and reliable VPN for secure browsing | ||
ZenMate Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |