Achieving business solutions by using VPN technology
- Various connections that require secured access
- The Considerations for Design Architecture of an effective VPN
- VPN solutions and investment considerations
Rapid technological advances make information the most valuable assent of a company. Keeping information secure is vital for business and enterprises. Yet communication of necessary information is essential to business and enterprises and solution, VPN based gives secure communications. Private Networks used to be the way of broad scale communication. Expensive, difficult to expand, difficult to maintain and manage; these networks were exclusively setup by business that could afford them. The internet offered an inexpensive alternative for communication but had problems of security of information. Site to site solutions, VPN solutions offered to take care of secure data transmission between various intranets and extranets. Roaming solutions, VPN gives clients better performance in security and confidentiality.
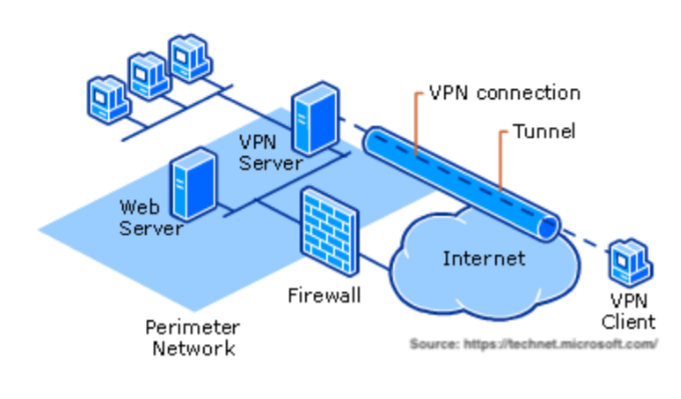
An authenticated and encrypted data transmission between two systems is what a VPN is all about. User’s privacy, Data Integrity and data authenticity is achieved through the various protocols adopted by VPN. Combining advances in tunneling, encryption and firewall technologies with good authentication mechanism we have an optimum solution in VPN. Tools of transparent setup and management along with flexibility and scalability have emphasized VPN’s gradual acceptance by business and enterprises. Intranets, Extranets or private networks VPN technology could be integrated seamlessly into the network. Secure access should be provided for connections like
- Network-to-network (site to site solution is needed)
- Desktop-to-desktop (Client solution of VPN is needed)
- Client-to-server (Server and Client VPN solution is needed)
- Dial-up for home office or traveling users (roaming solution of VPN is needed)
The Design Architecture of an effective VPN should consider
- Remote Access is essential in a tele working or home-office scenario. Secure tunnels through a dial-up or any other connection to the office is necessary
- Authentication of user’s identity is done by a variety of methods like passwords, smart cards, digital signatures, digital certificates etc. however none of them are entirely fool proof.
- Encryption to make information unreadable without special knowledge of a key or code. E-commerce, mobile telephony, automatic teller machines and private data need confidentiality. Encryption techniques can be emulated and cracked but it requires expert knowledge and takes a lot of time.
- Tunneling to establish a communication channel between two users such that no one else on a public domain can get access to the data transmitted. Even though there are protocols for tunneling, the idea of security in a tunnel exists; if it is truly from your machine to the other machine and does not end before your machine.
- Firewall is necessary to keep your computer or internal network segments secure from snooping or intruders or any other threat. It helps users to safely connect to the internet as well and implements security by allowing necessary traffic and blocking unnecessary traffic into and out of a network.
- Quality of Service (QoS) is necessary to guarantee that business critical applications get the required priority over non-critical usage like surfing the Web. This is done by ‘Bandwidth Shaping’ in VPN to enable quality of service to the many organizations that migrate from private networks.
- Digital Certificates and PKI solutions require ongoing management. This is a critical process due to sensitive nature of digital certificates as they are related to authentication and logging into the resources of the network. The overwhelming task of management can often offset the desired benefits expected. Automated digital certificate management provides an efficient means of management of digital certificates while ensuring enforcement of security policies.
- Encryption is computationally intensive software and hardware components should not affect the network’s throughput performance. In case of any server being affected in performance then a separate VPN server may be needed to improve the latency factor (time taken by the server to respond to a request).
- Management, monitoring, alerting, reporting, and helping is done at various levels in a given network by the administrator. The various log files help determine the user and the applications that have accessed VPN. These are separate and many software’s are coming out with performance management system for VPN’s
- Management features can be bettered to eliminate daily operations by incorporating automatic Key management, Auditing and Logging, SNMP-Simple Network Management Protocol and centralized management for security.
Continue to: VPN solutions and investment considerations
More on: internet business ideas

 | ExpressVPN Fast, anonymous browsing all over the world | |
NordVPN Enjoy online privacy and security with a reliable VPN | ||
 | Cyber Ghost Browse anonymously with reliable security | |
SurfShark Affordable and reliable VPN for secure browsing | ||
Private VPN Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |