Solutions for site to site VPN security products and options
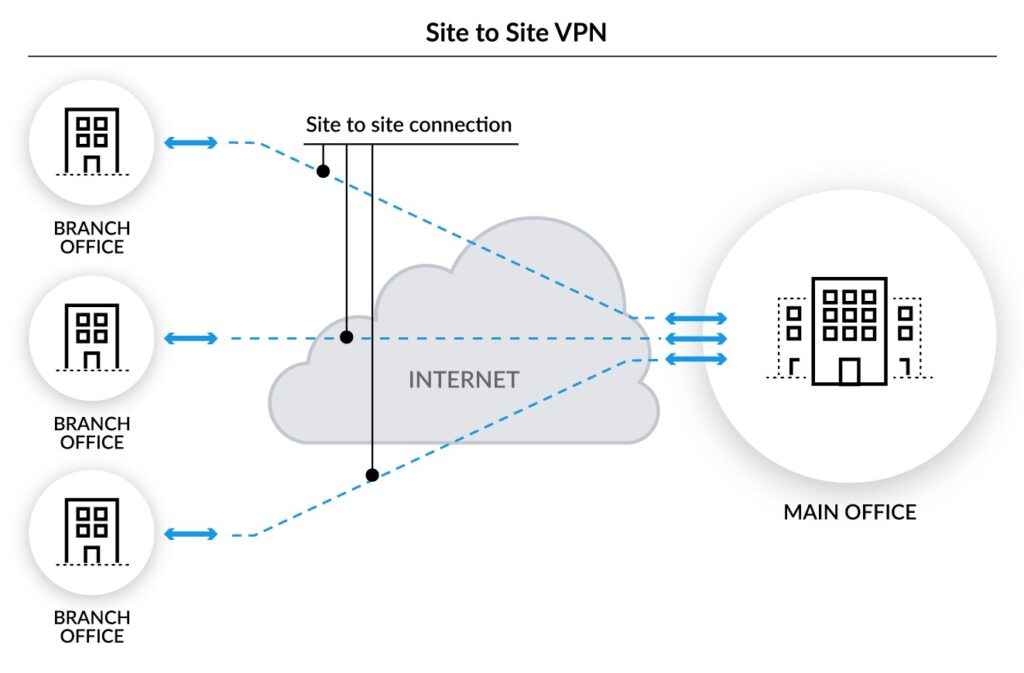
Traditional site to site connections were between to intranets or two Local area networks. These connections were leased, dedicated lines. These required constant management and its deployment was difficult. Affordable site to site VPN solutions have brought about secure broadband connections via the internet. The ubiquitous internet and VPN has brought cheer to ERP, CRM and many other businesses. As alternatives to the WAN infrastructure site to site VPN’s does not change the private WAN requirements. It meets WAN requirements like support of multiple protocols, high reliability and scalability at a lesser cost.
Site to site VPN solutions
Security of a general purpose computer cannot be guaranteed now days. New viruses and worms and malware spread via the internet. Many of those who use the internet are unaware of the threats to which their system is exposed. Large corporations cannot put up with these as they cause a huge loss to business. The options VPN’s offer toward this threat is based on software and hardware.
Software based VPN Firewall/Gateways
These systems have their inherent problems. They require a computer that has a faster speed of processing. The processing of data for security and VPN applications is very intensive and places demands on the computer which in turn slows down the network. For any business it is therefore optimum to have another server only for VPN transaction. The operating system is to be free from loopholes that crooks could manipulate to access data. It is therefore necessary that you constantly update and download security patches so that your network is not compromised. The server and its associated software’s, complexity and the management of the network are problematic issues for a business.
Hardware based Firewalls/VPN solution
These solutions exemplify security and also off-load the firewall and VPN processing from the server/computer. The security appliance protects the network at the internet gateway which is the VPN router and provides seamless local or remote management of security and remote access services. These security appliances are application specific integrated circuits which have powerful onboard processors handling the demands or firewall and VPN processing.
Unified Threat Management Systems
These devices are Firewall/hardware based solutions that intergrate a host of other functions like securing internet tunnels, filtering emails for spam and viruses, avoiding mails that involve in phishing, blocks spyware, detects and prevents attacks against specific applications that are vulnerable and filters URL’s as well. The company that sells these devices also sells gateway software to be run on a range of standard server hardware. Add on cards can be fitted into the existing machine so increase speed and also provide the additional security.
Intranet based Site to site VPN
Any business that has more than one remote location can used dedicated equipment that provides encryption and authentication to establish a VPN between both the sites. The branch office LAN can be connected to the central office LAN via the internet using a VPN solution. This connection of the tow LAN’s is called an intranet based site to stier VPN.
Extranet based site to site VPN.
One or more companies with intranet based VPN’s has a close cooperation with another company in providing specialized service to customers or suppliers can build a virtual private network that allows all of the companies to work in a shared environment over the internet. This type of a VPN is an extranet based solution to business enhancement. Continue to: Products for Site to Site VPN
| Port | Service |
| 20,21 | FTP (File transfer) |
| 22 | SSH (Remote login secure) |
| 25 | SMTP (Internet mail) |
| 53 | DNS (Host naming) |
| 80 | HTTP (Web) |
| 88 | Kerberos (computer authentication protocol) |
| 110 | POP3 (Client access) |
| 119 | NNTP (Usenet newsgroups) |
| 123 | NTP (Network time) |
| 137-139 | NetBIOS (DOS/Windows naming) |
| 143 | IMAP (Client access) |
| 161,162 | SNMP (Network management) |
| 163,164 | CMIP (Network management) |
| 443 | HTTPS (Web secure) |
| 514 | Syslog (Event logging) |
| 563 | NNTPS (Usenet newsgroups secure) |
| 993/tcp | IMAP4 over SSL, Internet Message Access Protocol |
| 995/tcp | POP3 over SSL, Post Office Protocol |
| 989,990 | FTPS (File transfer secure) |
| 1723 | Virtual private network (VPN) |
IP Addresses
TCP/IP stands for Transmission Control Protocol and IP for Internet Protocol. These protocols are responsible for transporting and managing the data across the network. The IPv4 requires a 4 byte address to be assigned to each network interface card that exists on all the computers in the network where as the Ipv6 assigns a 6 byte address. IP Addresses works almost like a house address without which determining where data packets go would be impossible. This assignment of address can be done automatically by network software’s such as the DHCP which is the dynamic host configuration protocol or by manually entering static addresses into the computer. The part of the IP address that defines the network is the network ID, and the latter part of the IP address defining the host address is the host ID.
Using this port and addressing scheme, the networking system can pass data, addressing information, and type of service information through the hardware, from one computer to another. Continue to: VPN ports and Hardware Ports

ExpressVPN Fast, anonymous browsing all over the world | ||
NordVPN Enjoy online privacy and security with a reliable VPN | ||
Cyber Ghost Browse anonymously with reliable security | ||
SurfShark Affordable and reliable VPN for secure browsing | ||
ZenMate Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |