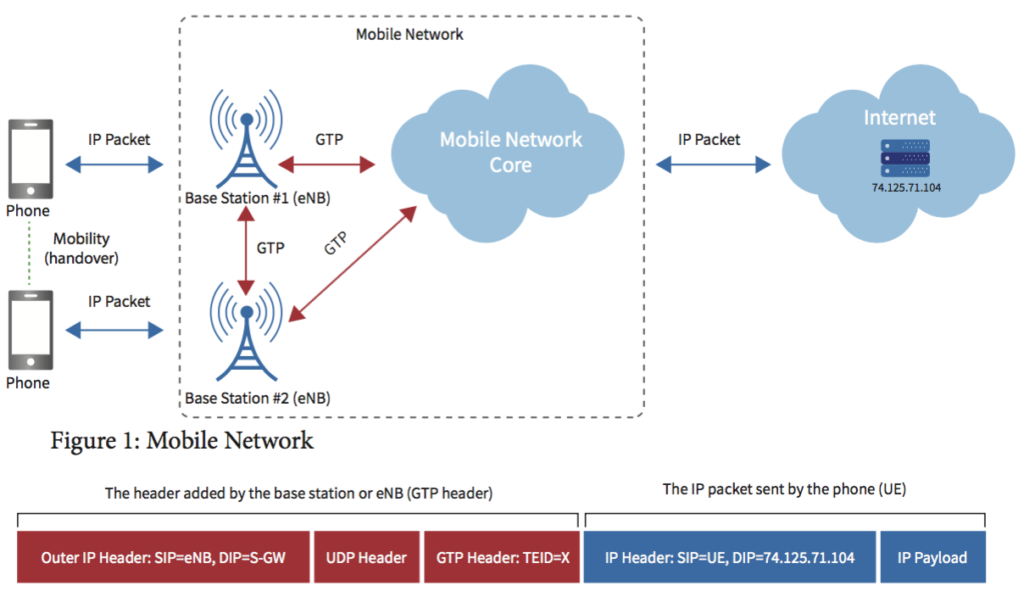
The Tunneling Protocol is a set of rules that allow information to flow between different networks. It creates a secure tunnel and repackages the data before it is sent. This makes it possible for a foreign protocol to run over a network. This method is commonly used for IPv6 and is compatible with IPv4 and IPv6-enabled devices. Its benefits are numerous and include increased security, faster connection times, and lower costs.

Another advantage is that tunnelling protocols are used for a variety of purposes, from international connections to bypassing firewalls. Because they enclose blocked protocols within allowed ones, they make it more difficult to perform ingress/egress filtering and deep packet inspection. Additionally, tunnelling is often used by malware and is not suited for sensitive information. For these reasons, it is important to choose a secure tunneling protocol.
Tunnelling protocols are used to send data over a public network. Most often, they are used to create a virtual private network (VPN), but they are also used to increase security of unencrypted data. The three most common tunneling protocols are Secure Sockets (SSH), Point-to-Point Tunneling Protocol (PPTP), and IPsec. This allows you to send unencrypted data across a network and maintain its privacy.
Some other tunneling protocols are also used for network security. GRE uses a network layer over network layer. The payload address of GRE packets is the same as the delivery network tunneling protocol, but there are some differences. For instance, a GRE packet has a different address for the payload. In L2TP, the payload address is the same as the delivery network tunneling process. This method uses the data link layer to transmit data between two nodes. It is a per-application VPN.
Tunneling protocols are also used to ship foreign protocols. For example, if you need to run IPv6 over IPv4, you can do so using a tunneling protocol. In addition to that, you can also use this technology to send SMS and MQTT over IPv4-enabled networks. This method is also known as VPN. This type of protocol works well with VPNs. Depending on the needs of your organization, the best protocol for your organization depends on your network configuration.
This type of VPN has several advantages. It is customizable and works on multiple platforms. It also has strong cryptographic algorithms and allows users to bypass firewalls. It also offers fast connection speeds. Among the various types of VPNs, PPTP is the fastest. It is not secure, and its security is limited. L2TP/IPSec is the most secure, but struggles with firewalls. It is a very secure tunneling protocol that is compatible with the delivery network.
While Tunneling does not involve tunneling, it does allow foreign protocols to pass through an IP network. This type of VPN prevents eavesdropping and data hijacking. By encapsulating the data packet as a payload, it allows it to travel over a nonsecure environment. Its main benefit is that it encapsulates the entire data packet as a single payload. This means that the original packet will remain intact, unless it is encrypted.
Tunneling protocols are essential for running IPv6 over IPv4 networks. Moreover, they provide greater security. While tunneling protocols are not as secure as a regular IP connection, they are still a great way to send data over the internet. By using a tunnel, users can access the same network as their local computer. For instance, a proxy server will not be able to spy on other users in the same network.
Tunneling allows remote users to connect to a network with security. A tunnel consists of a private network that can be accessed from anywhere. In general, tunnels are point-to-point, but multipoint tunnels can be created as well. In addition to ensuring the privacy of the data, it also enables the remote user to securely communicate with the server from any location. The best tunneling protocols can allow both clients and servers to communicate with each other, and they can also allow the users to collaborate.

 | ExpressVPN Fast, anonymous browsing all over the world | |
NordVPN Enjoy online privacy and security with a reliable VPN | ||
 | Cyber Ghost Browse anonymously with reliable security | |
SurfShark Affordable and reliable VPN for secure browsing | ||
Private VPN Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |