There are two technologies in particular which are in themselves becoming integral to IT operations and that are subsequently supporting the growth in BYOD – they are cloud computing and Virtual Private Networks (VPNs). Whilst there are many technology trends that are pushing the adoption of BYOD policies, these two are providing businesses with the key tools they need to overcome some of the challenges that BYOD brings with it.
Connectivity and Interoperability
The key to BYOD’s success is also one of its biggest hurdles and that is the variety of devices and platforms that it introduces into the IT systems equation. Users will be hoping to connect from a broad range of devices such as laptops, tablets and smartphones, running all manner of operating systems including the more traditional Windows, Mac OS and Linux alongside the newer kids on the block in the mobile sphere: iOS, Android, Windows Mobile and Blackberry for example.
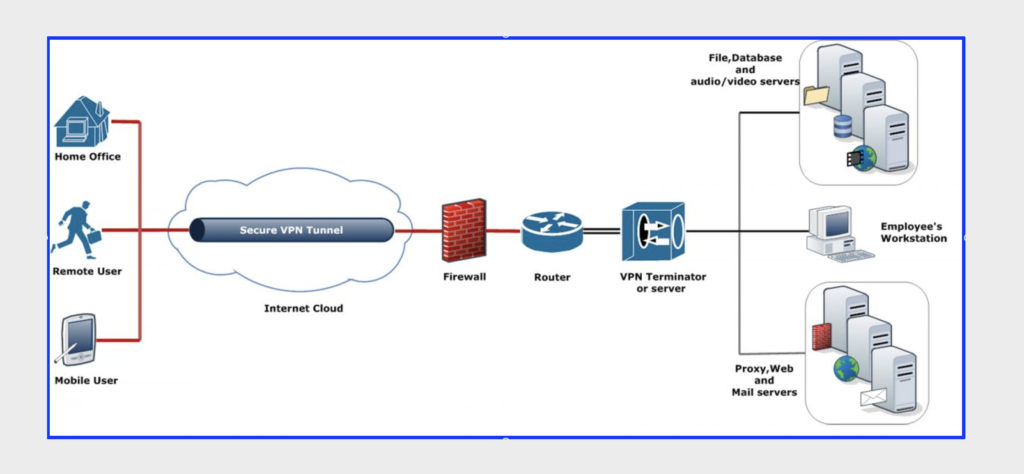
For organisations where the workers need to connect to the local network, VPN is the key. Tunnelling into a local area network across a VPN can allow users to access the files and/or control the applications on local (office) machines that they need for their daily work regardless of the device they are using, and their location, as long as they have an internet connection.
Although many applications have releases which support most operating systems it can be a real headache rolling out an application suit across such a variety of platforms. However, the all-conquering concept of cloud computing can offer a truly interoperable application solution. More specifically Software as a Service (SaaS) offerings, such a Google Docs or Microsoft Office 365, together with cloud storage, allow workers to operate within the cloud and therefore seamlessly between the office and on the go. Again, the only condition to use these services is that the user has an internet connection.
Security
Arguably the greatest challenge faced by organisations embracing BYOD is that of security; ensuring that personal devices aren’t compromised in themselves and don’t pose a security threat to the rest of the network. Allowing BYODs introduces many more vulnerabilities at various steps in the network and so there are many ways in which these risks can and need to be addressed.
The first step is to reduce the risk of the personal device being compromised in the first place. This is particularly pertinent where employees are bringing their own device in to connect to the businesses LAN. To achieve this, some organisations have conditions of use which require that the user’s device has specific anti virus and management software installed before it can be allowed onto the network. However, the risks can also be reduced by ensuring that personal devices are only allowed to connect to the local network via a VPN rather than a direct connection, even when the user is on site.
Using a VPN is a must for users in remote locations as the secure tunnel of a VPN prevents any information being intercepted in transit. It can be tempting for employees working off-site (or even on site) on personal devices to email documents, for example, backwards and forwards but the security of such communications can never be guaranteed.
What’s more that approach requires that at least some work data is stored locally on the personal device – a cardinal sin in terms of data protection. Again both VPNs and cloud solutions can negate the need to store local data. Using a VPN will allow the worker to operate on the local network, accessing, working on and storing everything they need on there, rather than on their own device. Secure cloud services on the other hand can be used to provide collaborative workspaces where users perform all their work in the cloud so that colleagues, wherever they are, can access it. However care should be taken to check the security measures used by cloud providers before signing up to such services whilst the user must also ensure that someone who misappropriates a device can’t then easily access their cloud account (through lack of device security and stored passwords etc).All this, plus implementing measures such as improved secure wireless networks in the work place, may result in greater spending on IT security and connectivity, but this should, as mentioned above, easily be offset by the direct and indirect financial benefits experienced elsewhere across the IT budget and the business as a whole.

 | ExpressVPN Fast, anonymous browsing all over the world | |
NordVPN Enjoy online privacy and security with a reliable VPN | ||
 | Cyber Ghost Browse anonymously with reliable security | |
SurfShark Affordable and reliable VPN for secure browsing | ||
Private VPN Experience the internet anonymously | ||
Purevpn Keep your data secure with a VPN built for privacy |